A hacker collective of self-described ‘gay furry hackers’ broke into America’s biggest nuclear power labs network system and stole records of thousands of employees.
The hacker collective called SiegedSec said on Thursday that it had hit Idaho National laboratory (INL) which is operated by the United States Department of Energy’s Office of Nuclear Energy. It said it stole employee social security numbers, physical addresses and bank account data. The hackers also boasted about breaching NATO’s IT security on two separate occasions this year.
The lab acknowledged that its HR systems had been attacked.
“On Monday, November 20, Idaho National Laboratory determined that it was the target of a cybersecurity data breach in a federally approved vendor system outside the lab that supports INL cloud Human Resources services,” said spokesperson Lori McNamara.
“INL has taken immediate action to protect employee data.”
East Idaho News confirmed the leaked information with several of the lab’s employees, which the collective had posted to its Telegram channel. Technically, the hacker collective has engaged in ransomware, but instead of demanding Bitcoin in return for the information, it’s asked for something far stranger.
“We’re willing to make a deal with INL. If they research creating IRL (in real life) catgirls we will take down this post,” the group said.
Certain corners of the internet frequently post memes about creating real cat-human female hybrids, but this isn’t the type of research the laboratory does. Historically, the lab has engaged in nuclear research but more specifically about the behaviour of nuclear reactors.
Read more: Terminally ill cybersecurity expert pleads guilty to hospital hack
Read more: Cisco secures US$28B deal to acquire leading cybersecurity firm Splunk
Group has targeted state and local government websites
Multiple organizations have erected over 50 reactors at the location. Among them are the ones that pioneered the world’s first usable amount of electricity from nuclear power and the power plant for the world’s inaugural nuclear submarine.
In addition to nuclear energy research, the lab also focuses on alternative energy solutions, actively working on improving electric vehicle batteries, protecting the power grid and designing small modular reactors.
It’s unclear what motivated SiegedSec’s attack. In its previous network penetration of NATO, the group attributed its actions to the military organization’s “attacks on human rights,” and added that leaking documents is also fun.
The collective has claimed responsibility for a series of network breaches on various government websites in five states that have enacted anti-trans legislation.
SiegedSec has targeted websites for state and local governments in Nebraska, Pennsylvania, South Carolina, South Dakota and Texas. The group most recently leaked data from the city of Fort Worth in Texas and pledges to continue these hacks to denounce what they perceive as the transphobic actions of government officials.
On its website, the group urged readers to “be gay, do crime,” while also celebrating their previous hacks. Thus far, the group has asserted responsibility for online attacks against the Nebraska Supreme Court, South Dakota Board of Commission, Texas Behavioral Health Executive Council, Pennsylvania Provider Self Services and South Carolina Justice Information Services.
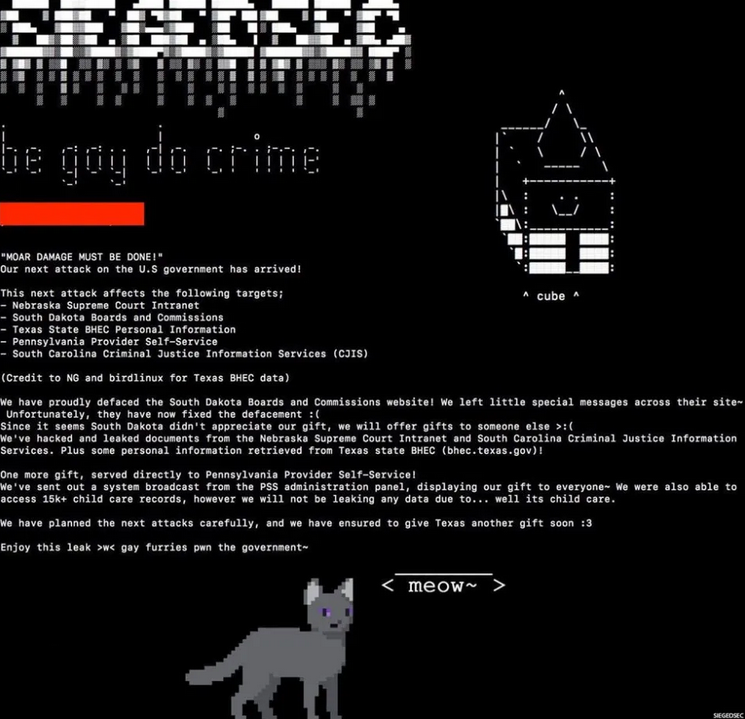
Image via SiegeSec’s website.
Read more: Qualys gets cybersecurity accolade for getting out in front of hackers
Read more: Blockchain Intelligence inks one year deal to track down cyber-criminals
Hacker collectives are usually state sponsored
Most hacks at the level of a government organization are state sponsored cyber-intrusions. Commonly, hacker collectives are tied to countries with adversarial relationships to the United States such as North Korea, China or Russia.
A few prime examples of institutional level data breaches include Solar Winds and Sol Oriens.
Microsoft President Brad Smith characterizes the SolarWinds’ attack on 18,000 businesses and US government agencies as ‘the largest and most sophisticated attack the world has ever seen.’
Cyber-attackers implanted malicious code in SolarWinds’ software in 2019.
When the Texas company distributed software updates, it inadvertently transmitted the compromised code to its clients, allowing criminals to access their business intelligence, nuclear secrets, and more. SolarWinds counted Microsoft (NASDAQ: MSFT), Mastercard (NYSE: MA), Visa (NYSE: V), Lockheed Martin (NYSE: LMT), and most Fortune 500 companies among its clients.
Russian hackers called APT29 or Cozy Bear, which are connected to Moscow’s foreign intelligence service are believed to be the culprit. Russia denies all involvement.
Sol Oriens is a bit different.
In 2021, a cyberattack targeted the US nuclear weapons contractor Sol Oriens, resulting in the loss of company intelligence and employee data. Sol Oriens assists Department of Defense and Department of Energy Organizations, Aerospace Contractors, and Technology Firms in executing complex programs.
The suspect is hacker collective Revil, which claimed to be selling four terabytes of Sol Oriens’ data in an online auction.
.
Follow Joseph Morton on Twitter
joseph@mugglehead.com